Hi everyone! Welcome to pentestguy. In this post we will explain how to bypass ssl pinning of android application using frida tools framework. There might be multiple way to achieve ssl pinning bypass but frida and objection work like a butter.
Our testing playground for this mission is the AndroGoat app, known for its vulnerabilities. You can download AndroGoat from this link If you’re new to installing AndroGoat, Frida, and Objection, please refer to our previous post for guidance here
Setting up a Burp Proxy for Android:
To get started, we need to configure a Burp Proxy on our Android device. Please note that I’ll be using Android Studio for this setup.
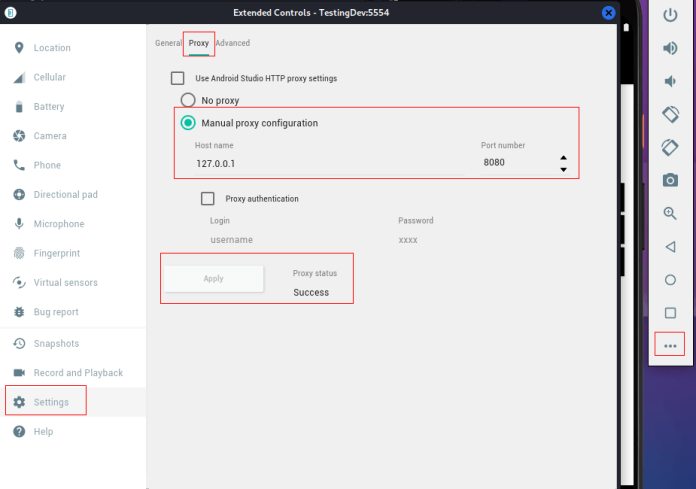
Open Burp Suite and navigate to the Proxy section. You can either add a new port along with 127.0.0.1 or leave it as the default, which is on port number 8080.

In this case it’s default
In your device settings, navigate to the proxy section and add the proxy along with the port number as specified.
Download the Burp certificate to your local device and rename the extension from “cacert.der” to “cacert.crt”. After that, simply drag and drop it onto your Android device.

To install the certificate, go to Settings > Security > Encryption & credentials > Install from SD card. Browse for the certificate you dropped earlier on the device and install it.

Now that we’ve set up our environment, let’s explore two methods to bypass SSL pinning in Android apps.
Road 1: The Way of Objection
For this method, you’ll need the package name of the target app, which can be obtained through ADB or Frida:
Using ADB:
adb shell pm list packages | grep owasp

Using Frida:
frida-ps -Uia

Before bypassing SSL pinning, try opening AndroGoat and navigate to the Network Intercepting section. Click on CERTIFICATE PINNING and attempt to capture the request in Burp. You’ll notice that it doesn’t work as expected.

Once you have the package name in hand, utilize Objection to bypass SSL pinning. Replace ‘owasp.sat.agoat’ with your target package name:
objection -g owasp.sat.agoat explore
android sslpinning disable

To verify whether SSL pinning has been bypassed, click on CERTIFICATE PINNING and you should now be able to capture the request.

Road 2: The Way of Frida Script
Here, instead of running a script directly from CodeShare – https://codeshare.frida.re/@akabe1/frida-multiple-unpinning/ , save it as a plaintext file. You can get the script here. Replace ‘owasp.sat.agoat’ with your target package name to run the command:
frida -l sslby.txt -f owasp.sat.agoat -U

Again, to confirm whether SSL pinning has been bypassed, click on CERTIFICATE PINNING, and you should now be able to capture the request.

And there you have it, a guide to bypassing SSL pinning in Android apps using Frida and Objection.
If you found this post helpful then please share it with your co-workers and friends. Please provide your valuable comment and let us know if there is any suggestion. Now you can also collab with us please check our collaboration page, thank you!
